Are you a computer science or IT student searching for good research topics for your technical assignment? Well, instead of considering the frequently discussed computer topics, without any hesitation, give preference to the latest cybersecurity research topics. Cybersecurity is an advanced technology that focuses on the protection of networks, data, computer systems, technologies, and devices from serious cyber-attacks.
In recent times, the world is highly dependent on the Internet and digital technologies. Particularly, people are more comfortable using internet-based applications for their daily use including bank transactions, food delivery, online shopping, etc. As the usage of the internet and online applications is increasing day by day, some criminals use several attacking methods to steal the user’s personal data. So, to handle such security issues, nowadays almost all application developers give utmost attention to strengthening online security and safety. Also, various research activities are being performed in the field of cybersecurity to prevent critical security problems that arise online.
Basically, cybersecurity is a vast and complex technology-based subject with different research topics to explore. If you have an interest in preparing a cybersecurity research paper, then continue reading this blog post. Here we have suggested a list of great cybersecurity research topics and ideas to consider for your computer science assignment.
List of Cybersecurity Research Paper Topics
To write a research paper, a good topic is necessary. Currently, do you have to submit a cybersecurity research paper? If yes, then you will have to first search and identify a captivating research topic on cybersecurity. For writing a cybersecurity research paper, you can take into account the following research areas- AI and IoT security, data privacy, space communication, quantum technology, cyberethics, and criminology.
In general, each research area would have many dissertation topics to focus on. So, you need to invest more time and effort to hunt for a research topic matching your interest.
As it is challenging to search and gather the research ideas, here we have grouped different categories and have presented some unique cybersecurity research topic ideas. Explore the complete list and choose the right topic that you have strong knowledge of.
Simple and Easy Cybersecurity Research Topics
- What are phishing scams and how do they work?
- Explain the advantages and disadvantages of antivirus software.
- The dangers of connecting your device to a public wireless network.
- How to restore lost data?
- The dangers of automotive hacking.
- How does working remotely affect the security of companies?
- What are the ways of securing removable media?
- Define brute force attack.
- How to remove malware from a Windows computer?
- What is the role of passwords in the authentication process?
- How to recognize a social engineering attack?
- Latest innovations that are a threat to cybersecurity.
- Dangers of improper access controls.
- Is hacking becoming a global epidemic in the digital world?
- Can organizations use impenetrable network systems?
- Vulnerabilities of modern networks to intrusion.
- Analyze human behavior in cybersecurity.
- Best mobile protection for your smartphone.
- Explain the role of the system administrator.
- How to secure your home Wi-Fi?
- Application of Digital Forensics in cybersecurity
- Discuss the difference between Penetration Testing and Red Teaming
- Detecting and mitigating the gatekeeper user override on macOS in an enterprise environment
- Automating RMF (risk management framework) steps using lightweight scripts and tools
- Analysis of the NIST (National Institute of Standards and Technology) Cybersecurity Framework
Application Security Research Topics
- Discuss data leaks in mobile apps.
- AI applications: ethical limits and possibilities.
- Explain SQL injection attacks.
- What is the insecure deserialization effect?
- Discuss the importance of backend access control.
- Dangers of XSS attacks on apps.
- Malicious apps on Google Play.
- The best application security testing practices.
- Poorly configured security protocols.
- Benefits of logging for applications.
- Importance of implementing scalable security for devices without 802.1x support for authenticating computers
- Application of enterprise observable security using Microsoft Azure
- Why it is crucial to overcome AMSI (antimalware scan interface) integrated with most endpoint security solutions?
- Application of a multi-leveled approach to detect coercive malicious documents employing OCR (optical character recognition)
- Compare and contrast the application of firewalls, antivirus systems, cloud security, and data encryption
Computer Security Research Paper Topics
- What is the role of digital literacy in preventing hacking?
- How to block a network intrusion before it causes any effect?
- Why ordering software from the black market is a threat to security?
- What happens during a system breakdown and maintenance?
- Design a robust cybersecurity system.
- How does a ransomware attack work?
- How does Facebook protect itself from cyber-attacks?
- Infiltrating a Mac OS X operating system.
- Cyber-attacks and national security risks.
- The implication of private email accounts in data breaches.
Research Topics on Cybersecurity Ethics
- What are IoT attacks?
- Recent Ransomware attacks.
- How to defend against DDoS attacks?
- Worst software vulnerabilities in the Windows OS.
- Social hacking dangers.
- Why should cyberethics be different from real-world norms?
- Machine learning is used in computer viruses.
- What are endpoint attacks?
- Signs of a phishing attack.
- How to defend against cross-site scripting attacks?
Data Security Research Ideas
- Discuss physical data security.
- The best authentication methods.
- Examine the mobile landscape regarding data security.
- The dangers of phishing attacks.
- Explain the significance of frequent system updates for data security.
- Explain the importance of backup and recovery.
- How to conduct data erasure procedures?
- Talk about cloud security.
- Explain the relationship between privacy and data security in computing.
- Complex mobile device security methods.
Read more: Interesting Big Data Research Topics for Students
Research Topics on Cyber Crime
- Discuss the effects of technology evolution on cybercrime.
- Track the evolution of online scams.
- How does website spoofing work?
- Should governments punish cybercrimes like real-life crimes?
- Compare various types of fraud methods.
- Worst cases of IoT hacking.
- Discuss the vulnerabilities of card payment data storage.
- The dangers of corporate data theft.
- What is cyber extortion and how does it work?
- Discuss ransomware attacks on hospitals.
Outstanding Cybersecurity Research Topics
- Explain cross-site request forgery attacks.
- The benefits of implementing multi-factor authentication.
- Artificial intelligence security systems.
- The use of biometrics as a cybersecurity method.
- What is cyberterrorism?
- Discuss the effects of logging in to many devices at the same time.
- Describe the effectiveness of cybersecurity audits on company systems.
- The role of studying mobile platform security.
- Evaluate the significance of computer forensics.
- What legal frameworks work best for a computer company?
- The latest cloud security threats.
- The role of YouTube in contributing to the rising number of hackers.
- Is online slander a cybercrime?
- Compare the security of UNIX and Ubuntu.
- What are the effects of using cracked computer software?
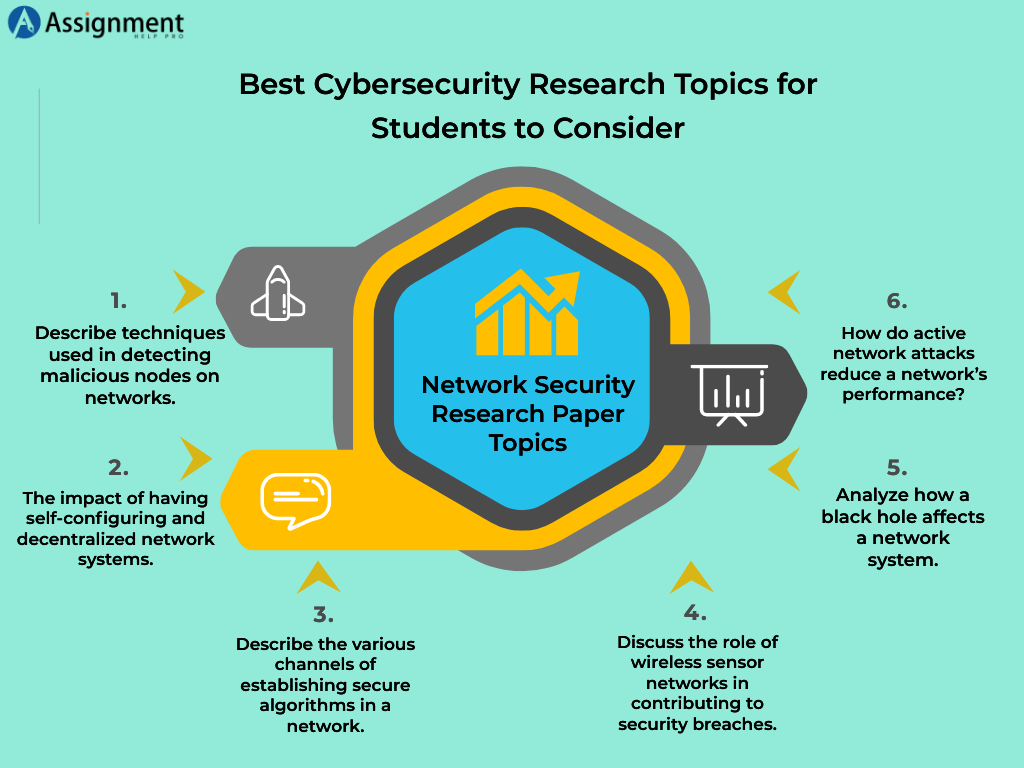
Network Security Research Paper Topics
- What is behavioral analytics and how does it work?
- The best 3 tools for excellent email security.
- Discuss the applications of Hyperscale Network Security.
- Describe techniques used in detecting malicious nodes on networks.
- A closer look at access control best practices.
- The impact of having self-configuring and decentralized network systems.
- Describe the various channels of establishing secure algorithms in a network.
- Discuss the role of wireless sensor networks in contributing to security breaches.
- Analyze how a black hole affects a network system.
- How do active network attacks reduce a network’s performance?
- How do modern Intrusion Prevention Systems work?
- Preventive measures against a distributed denial-of-service attack.
- The importance of keeping your software up to date.
- Network segmentation and its applications.
- Discuss the most effective Data Loss Prevention systems.
Information Security Research Topics
- Discuss the strengths and weaknesses of current authentication methods.
- The importance of data storage centralization.
- What is cyber espionage and why is it dangerous?
- Discuss secure quantum communications.
- Explain the effective cybersecurity methods in the Internet of Things.
- How to strengthen the firewall of an information system?
- The best 5 algorithms for data encryption.
- How to detect malicious activity on a system.
- Discuss the implications of Wi-Fi hacking apps on mobile phones.
- The effects of using your image on social media.
- Black hat hackers vs. grey hat hackers.
- The role of pseudo names and nicknames on social media.
- The dangers posed by unprecedented attacks.
- Explain the role of information communication technologies in maintaining security.
- Discuss the impact of sharing personal details with hiring agencies.
Operational Security Research Topics
- What is the role of OPSEC in a company’s cybersecurity efforts?
- Application of appropriate OPSEC measures at Facebook.
- The process of identification of critical information.
- The use of OPSEC in the U.S. Navy.
- An in-depth look at the analysis of vulnerabilities.
- Explain the importance of Security Awareness Training.
- Compare COMSEC with OPSEC.
- Methods of conducting a thorough assessment of risk.
- The Role of the Overarching Security Policy.
- What is the analysis of threats and how is it done?
Cyberbullying Research Ideas
- Would cyber communism decrease bullying?
- Feminism and the fight against cyberstalking.
- Gender differences in the perception of online abuse.
- What is the role of Facebook in advancing cyberbullying and hacking?
- The importance of parental control mechanisms on children’s computers.
- Stopping cyberbullying in the EU.
- Discuss the relationship between cyberbullying and cybersecurity.
- How dangerous is cyber-stalking?
- Why are teenagers more victims of cyberbullying than adults?
- Best ways to protect yourself from cyberbullying.
Excellent Cybersecurity Research Topics
- What are the various types of security exploits?
- Explain the role and function of a vulnerability scanning tool.
- How does a key logger work?
- What is a packet sniffer and how does it work?
- Talk about the basic architecture of a computer virus.
- Discuss the importance of a reliable disaster recovery plan.
- How does a firewall actually work?
- Explain the role of IT governance on value delivery.
- The role of globalization in enhancing cybersecurity.
- Cookies and your privacy online.
- Terrorist groups and the cybersecurity threats they pose.
- Discuss why fingerprints are the best method of protecting devices.
- The role of NGOs in combating cyber terrorism.
- Analysis of the Stuxnet virus.
- The human factor in cybersecurity applications.
Cyber Law Research Topics
- Discuss cybersecurity laws in China.
- Loopholes in cyber laws make the practice challenging to curtail.
- Discuss the importance of the Cybersecurity Information Sharing Act.
- Why is it necessary to review the data protection laws?
- How should law enforcement adapt to online technologies?
- Does the internet need a government?
- The rule of law in real life versus in cyberspace.
- Cybersecurity laws and regulations in the European Union.
- The importance of the brand new CISA Cyber Exercise Act.
- Discuss trending topics in cyber law of the past ten years.
Interesting Cybersecurity Research Topics
- Discuss the pros and cons of various cryptographic methods.
- Explain the phases of a Trojan horse attack.
- Explain the role of prime numbers in cryptography.
- What does a VPN do?
- Explain the various data extraction techniques.
- How does cryptojacking work?
- Compare the encryption technologies of various social networks.
- Describe the mechanics of password protection.
- Examine how GhostNet operates.
- Big data and the rise of internet crimes.
- Pros and cons of various infosec certificates.
- What are the dangers of public Wi-Fi networks?
- Discuss the role of hackers in modern warfare.
- How to recover data from a broken hard drive?
- What are man-in-the-middle attacks?
- How did the WannaCry malware work?
- Discuss the effects and solutions of Catfishing.
- Explore the ethical side of whistleblowing.
- Is jailbreaking a crime?
- How can online consumers protect themselves from fraud?
Unique Cybersecurity Research Topics
- Why should you bother about the security of your mobile device?
- How to counter-terrorism with advanced cybersecurity measures.
- Discuss the security threats associated with WordPress websites
- Why using Cyber Cafes may be detrimental to your digital security?
- Discuss the impact of reverse engineering on computing systems
- Explain the role of data encryption technologies in ensuring system security
- Analyze the threats that biometrics are bringing to digital systems.
- How to detect apps that invade your privacy unknowingly.
- Explain the impact of online persuasion campaigns on cybersecurity.
- Discuss the factors that lead to the global nature of cyber attacks.
- How to prevent automotive software from malicious cyber attacks
- How do online hackers collect information without the knowledge of the victim?
- Why is it challenging to maintain endpoint security?
- How does RSA increase the safety of a particular network?
- Why is it difficult to detect a passive network attack?
Conclusion
In case, you are still confused about what topic to select or how to write a cybersecurity research paper, quickly reach out to us. Just book your assignment order on our website to complete your work ahead of the deadline and as well earn other scholastic advantages.